Why are security zones so important for ISO 27001:2022?
With the switch to the 2022 version of ISO 27001, the term “security zone” will appear more and more frequently in the certification audit of an ISMS. Here we would like to explain what exactly is meant by a security zone and how to correctly map it in an ISMS context.
What is a security zone?
A security zone is an area in the company network. You can often see the IT department representing the segments according to the onion ring principle. Even in simpler networks, individual systems can be grouped into zones and color-coded. In the further sections of this article, we will show examples of how this can be shown graphically.
If we want to define the zones, we have to assign properties to each zone. For example, a red zone could be the most important. In the red zone, we might find our ERP, CRM, HR and database servers. In the yellow zone, we find important systems that do not contain extremely critical data. In the green zone, only our notebooks and smartphones are in the green zone. Since we store all data on the central server, the loss of a notebook is not as critical as, for example, the loss of the database server (red zone).
We can therefore classify the colour zones as follows:
- White zone = public
- Green zone = controlled zone
- Yellow zone = restricted zone
- Red zone = high-risk zone

What does a concept of physical security look like?
When we create a physical security concept, we need to define the security zones. This allows us to classify our systems into the correct zones.
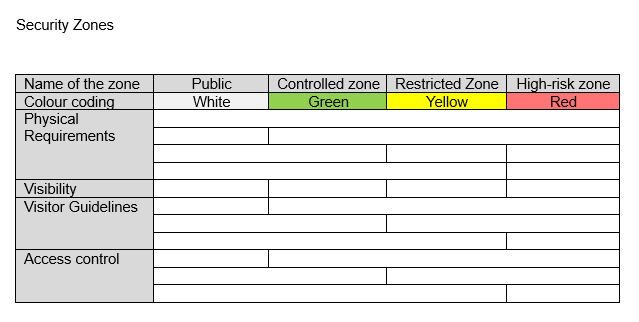
We need to define the following for a security zone:
- Name of the zone
- Colour marking
- Physical requirements
- Access control
- Visibility
- Visitor requirements
It is best to create a table in your ISMS documentation in which you define the above points. This makes it easier for employees and auditors to understand how you apply the security zones to your physical security concept.
How do I draw a security zone for my ISMS?
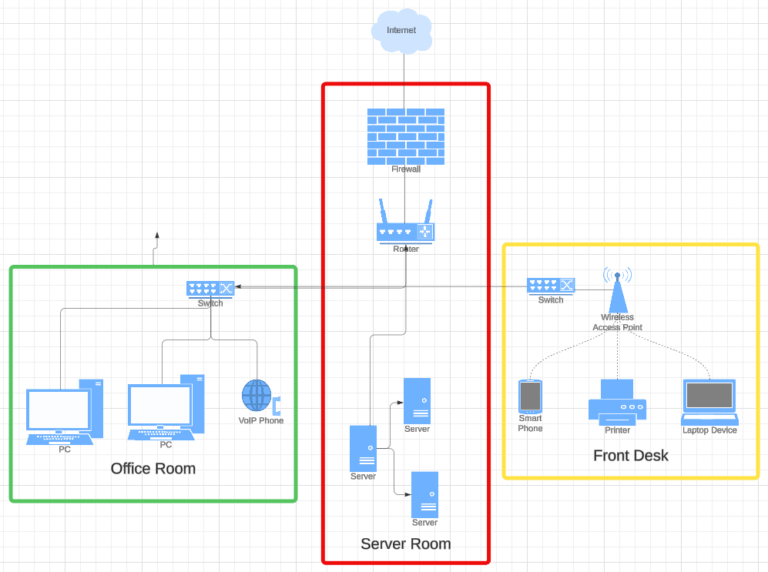
In the following example you can see the 4 zones (red, yellow, green, white). The red zone represents our server room. This is where the internet access, the router/firewall and 3 servers are located. The yellow zone would be the entrance area where our reception is located. There may be a workstation there and a television with the latest news. Suppliers, postmen, customers and other visitors occasionally enter this area. Our green zone represents the office area where no public traffic takes place. This is where most employees work on their networked desktops or laptops. This is where software is developed or customer inquiries are handled over the phone. The human resources department or purchasing department may be located here.
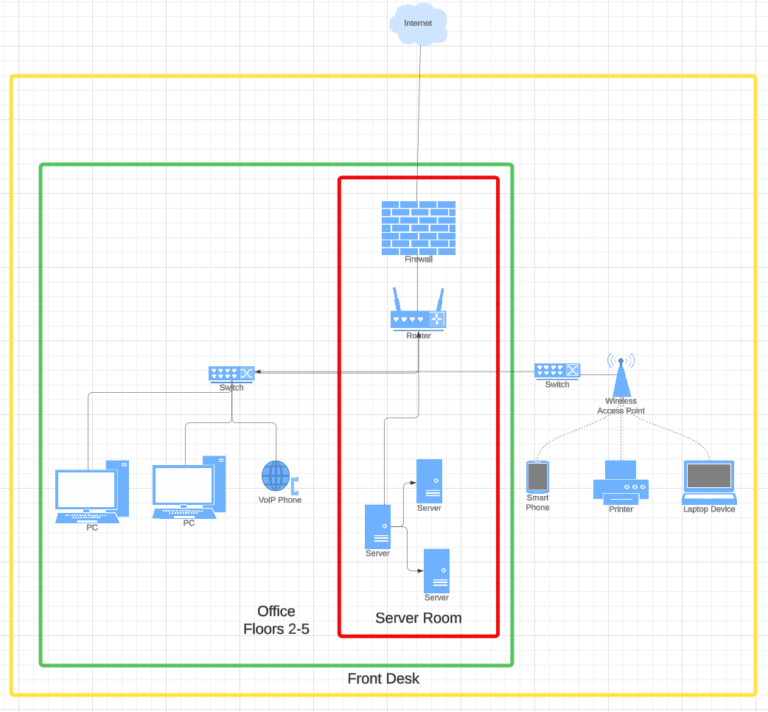
In the following example we see a security concept that represents the security zones like onion rings or tree rings. Anyone in the yellow zone cannot simply get into the green zone. In the green zone the workplaces are located on 4 floors. Only those who get in here can request entry into the red zone.
How do I display security zones in a table?
As already mentioned, auditors from certification bodies are increasingly asking for the definition of security zones. First, you have to describe the physical security concept in detailed text sections. Then you can define these zones in bullet points or short sentences in a table and specify their rules.